Cloud-managed Zero Trust Security & Networking Services for the Modern Enterprise
Deployed as a managed SaaS, Airgap deploys in hours with built-inSecure access, Microsegmentation, and Discovery.
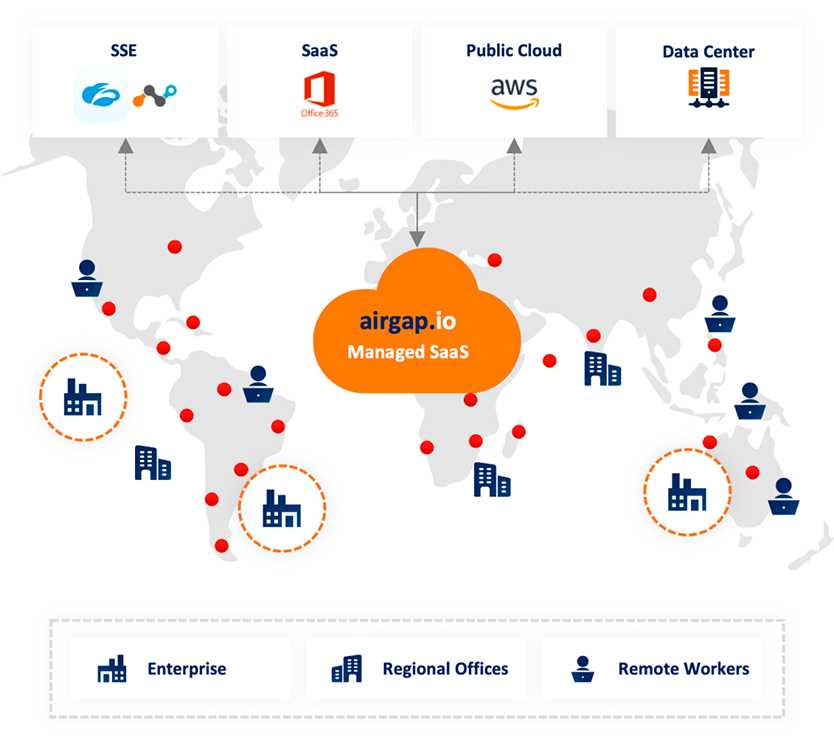
The Airgap agentless architecture provides total protection for business-critical infrastructure by authorizing every transaction and segmenting every endpoint. Reduce risk, improve compliance, and get higher machine uptime, all with full east-west and north-south visibility.
Secure Access →
Prevent threat proliferation from users to machines. Enforce identity-based restricted access.
Microsegmentation →
Perfectly segment every endpoint and instantly stop lateral spread.
Built-In Discovery and Visibility →
Real-time accuracy for all assets with full east-west visibility.
Single Solution for Securing the Enterprisewith secure access, segmentation, and asset discovery
Secure Access
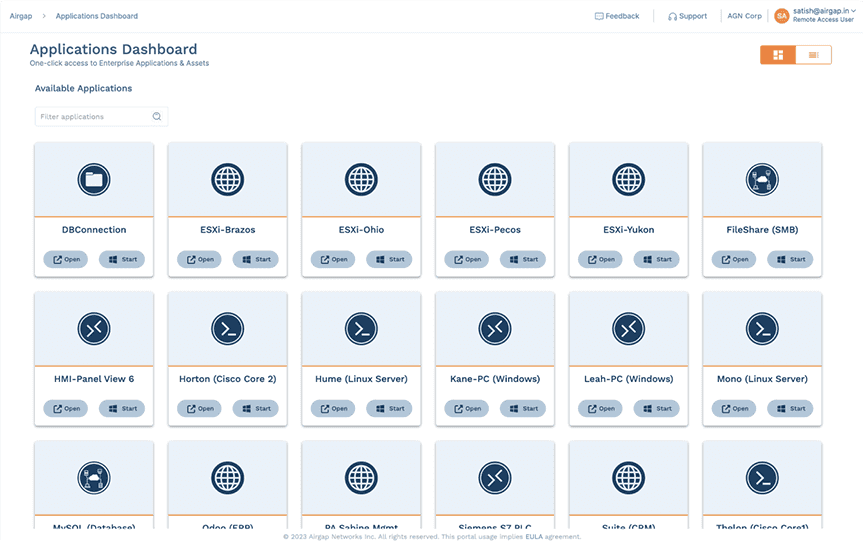
Disposable Jump Box
Say goodbye to jump host cost and complexity
- SaaS managed service
- 30% to 50% typical cost savings
- Agentless
- Enhanced security – leaves no attack surface
- Dissolves after use – better than moving target
- Works with or without VPN
- Per user or enterprise annual subscription license
- SSO/MFA identity check with end-to-end encryption
- Lockdown from User IP to Machine IP
- Compliant, regularly patched
- Cloud/AWS scale
- Per-application customized templates
- Clean, patched, compliant image every time
- New instances spun up in the cloud on-demand
- No open ports for attackers
- Maximized network performance
- Time-to-value less than one hour
- Built-in visibility and discovery
Segmentation
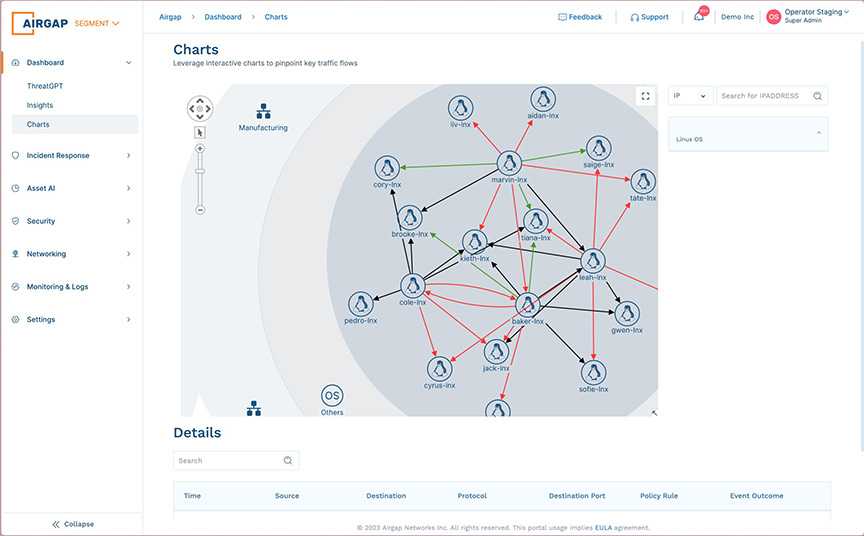
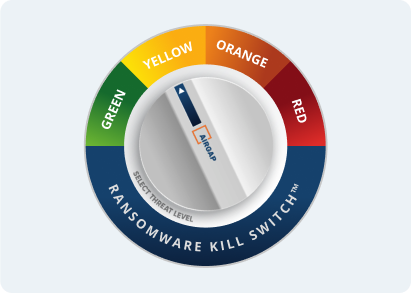
Ransomware Kill Switch
Say goodbye to ACLs/NAC configuration headaches
- Stop lateral threat by segmenting every endpoint
- Fully segment legacy servers, headless machines, and cloud-hosted assets
- Advanced threat detection
- Granular incident response
- Fully managed
- Deploys in hours
- No hardware upgrades or VLAN/IP readdressing
- Built-in NAC and DHCP
- Dozens of integrations
- Physical or virtual appliances
- Phased deployment, pay-as-you grow
- Hitless upgrades
- No open ports for attackers
- Maximized network performance
- Automated policy grouping and tagging
- Built-in visibility and discovery
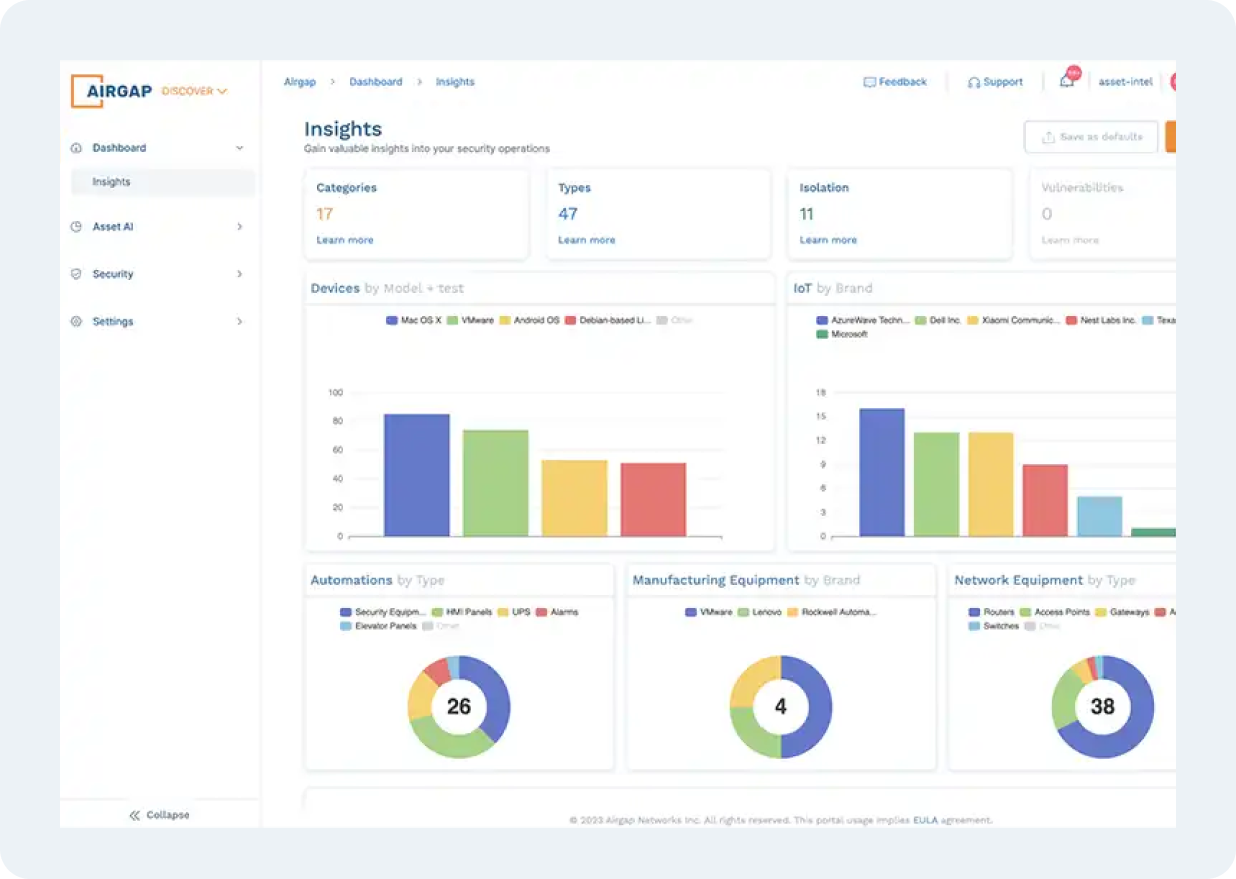
Asset Discovery
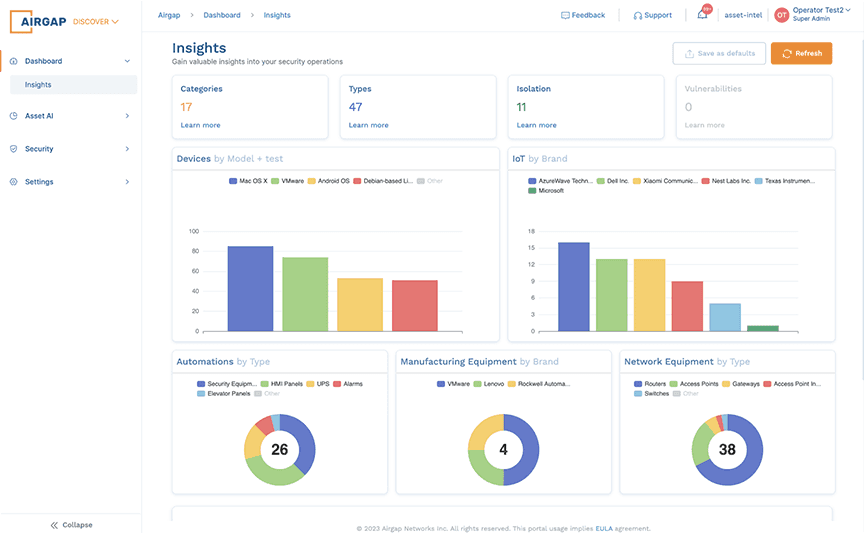
Discovery and Visibility
Say goodbye to visibility gaps and inaccurate inventories
- Real-time, highly accurate asset discovery
- Built-in to the Airgap managed SaaS
- Fully programmable data pipeline
- Intuitive interface for natural language queries
- KPI-aligned
- Search network assets like the web
- Integrated Grafana for instant dashboards
- End manual & offline documentation
- Real-time automapping and topology
- Network-aware algorithms
- Query, tagging, and alert monitors
- Simple deployment
- Many integrations
- Fully unified data for single source of truth
- Advanced analytics
- Logical entity groupings
- Context-rich predictive analytics
Airgap
at Enterprise scale
Delivering the performance and availability needed for today’s modern enterprise
32
countries
4K
sites
4M
network elements
22B
metrics/day
75M
syslog records/day
22T
flows/day
Customer Stories
Hear what our customers say
“We went from the first meeting, to becoming a customer, to microsegmenting our entire footprint in just under a week. That is unheard of”

Airgap IntegrationsDeploys seamlessly into your existing security stack

SentinelOne

CrowdStrike
Splunk

ZScaler

Okta

ELK

Armis

PagerDuty
ServiceNow
Microsoft Entra
OneLogin

Azure AD
Airgapfor easier compliance
Airgap is the fastest solution for achieving the two hardest zero trust compliance requirements - secure access and segmentation. Check the box on these zero trust hurdles in hours.
Operational SimplicityEasy and intuitive management
ResourcesLearn how Airgap can help

Why Microsegmentation is Core to Endpoint Security in 2023

Disposable Jump Box

Airgap Zero Trust Enterprise
Shrink attack surface, lower costs, and improve business uptime with Airgap managed SaaS..