
Resolve To Get in Zero Trust Shape in 2023
Resolve to be stronger in the face of more severe, malicious attacks coming in 2023 by segmenting networks now to reduce collateral damage and attackers’ lateral movement. Hardening legacy tech stacks alone doesn’t go far enough to stop and contain ransomware and malware-less attacks.
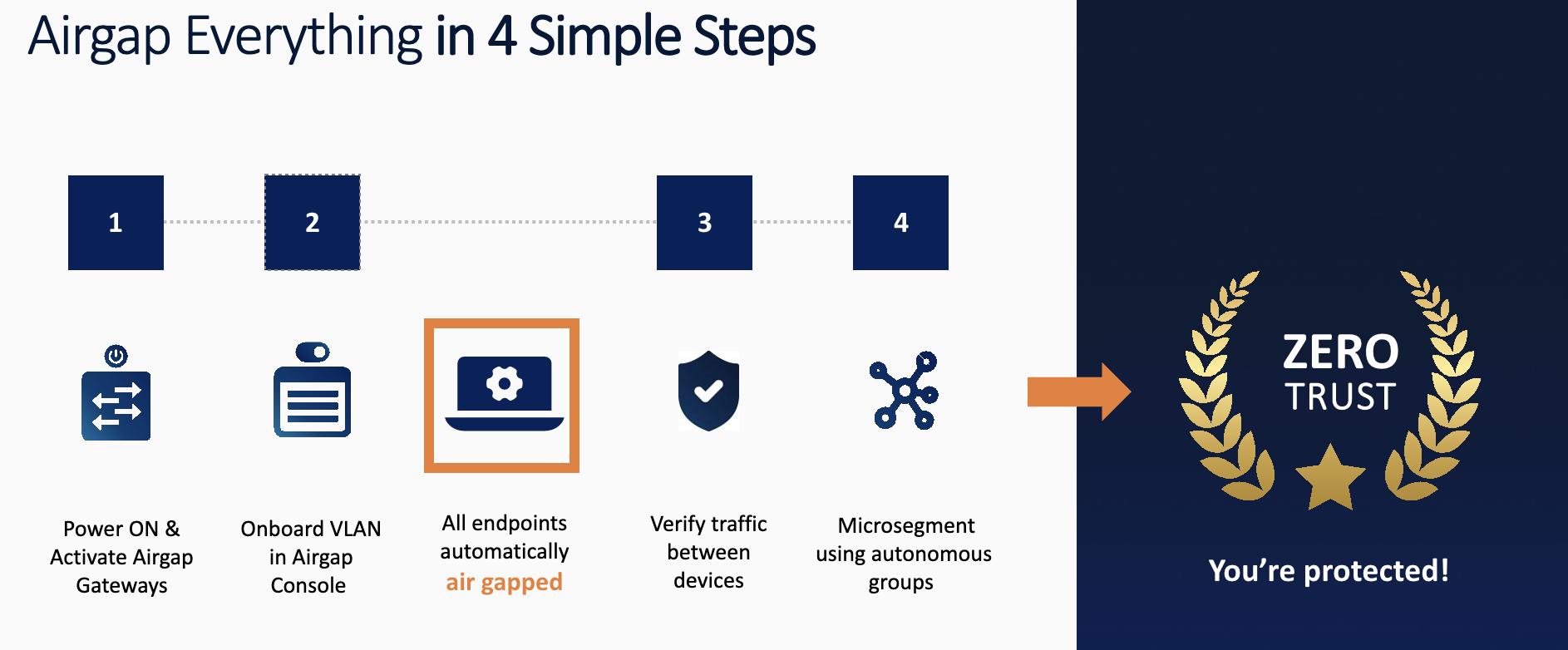
Pursuing a zero trust security strategy starting with microsegmentation does. It’s also core to pursuing a zero trust initiative as defined in the NIST SP 800-207 Zero Trust framework. Microsegmentation has proven effective in eliminating lateral movement across networks and reducing the total attack surface of an organization.
Resolve To Be Stronger At Zero Trust
Having a breach mindset is key to getting stronger at zero trust. Assuming intrusion and breach attempts are inevitable is a strong motivator for IT and cybersecurity teams to sharpen their zero-trust security strategies, skills, and knowledge.The goal is to make zero trust an integral part of an organization’s muscle memory. The best way to accomplish that is by resolving to get zero-trust initiatives and strategies in shape.
Getting stronger at zero trust doesn’t just happen. There needs to be a plan for how, where, and what needs to become strongest first. Nearly every CISO tells me that endpoints are the weakest link in their networks. Attackers capitalize on the weakest endpoints they discover by scanning network ports to gain access and move laterally across networks. As one CISO told me, “there’s good-enough security in legacy systems that we patch, and then there’s zero trust strong, where we’ve taken more control of our attack surfaces and endpoints and know we’re shutting down intrusions.”
How To Become Zero Trust Strong Starts With Microsegmentation
Defining your fitness program to become stronger at zero trust needs to start with the weakest security areas to turn them into strengths. Fencing endpoints using outdated technology is a weakness that needs to be turned into a strength. Microsegmentation doesn’t need to be complex or expensive to get right.
Airgap Networks implemented microsegmentation for a leading specialty retailer of casual apparel, operating hundreds of stores in across the nation. The customer's zero trust requirements included achieving more granular segmentation for IT compliance and enabling Single Sign-On (SSO)/Multi-factor Authentication (MFA) for mission-critical assets across their hybrid workforce and external partners. The customer also needed to accelerate its zero trust deployments and policy management. Most importantly, the customer wanted greater visibility and control of lateral traffic across 100% of their constantly changing endpoint footprints.
Airgap’s Zero Trust Everywhere solution is a perfect fit for the customer because it quickly addresses the security areas they need to turn into strengths. Foremost among those is the constantly changing endpoints that together comprise the most fluid attack surfaces the company has. AirGap now has 100% of the customer's corporate endpoints across their data center, corporate headquarters, and retail stores fully microsegmented, along with fully implemented Zero Trust Network Access (ZTNA) for their hybrid workforce and partners.
Airgap Everywhere is built using standards-based technology that is 100% compatible with an enterprise’s existing tech stack footprint. No agents or network changes are needed.
CISO’s Microsegmentation Lessons Learned
Cybersecurity is now a business decision, and every project needs to deliver value beyond deterrence to protect customer, employee, and partner identities, data, and transactions. CISOs tell me they defend zero trust budgets by showing what will happen to customers, employees, and company revenue if the attack surface isn’t reduced and identities aren‘t protected. CEOs and boards of directors are concerned about the impact of a breach on their brands – and the loss of customer trust during these turbulent economic times.
Getting zero trust strong is the way through these challenges, according to CISOs. How they’re getting in zero trust shape is as varied as their businesses are. Yet they all share an intensity to improve zero trust security, tackling microsegmentation early.
Here are their lessons learned:
- Choose a microsegmentation platform that can scale to secure on-premise and cloud components of your security tech stack at scale. A few of the CISOs I’ve spoken with say that one of the challenges they’ve faced implementing microsegmentation is protecting on-premise and cloud apps and platforms. For many organizations, hybrid cloud, multicloud and private cloud configurations typify their IT infrastructures. Airgap’s Zero Trust Everywhere is born in the cloud, can protect hybrid and multicloud configurations, and can be part of an organization’s playbook for managing least privileged access and ZTNA permissions network-wide.
- Overburdening endpoints with agents leaves them more vulnerable to scans and attacks, while Airgap achieves zero trust using network gateways. One CISO told me they have an average of eleven agents on every endpoint device on their network. Attackers scan their endpoints, looking for software conflicts and breakdowns in coverage. Multiple intrusion attempts happen every week on their overcrowded endpoints as a result. Instead of doubling down on more agents, the CISO spoke to Airgap about how they could reduce their attack surface. Airgap Zero Trust Everywhere makes sense for them because our solution modifies the subnet mask of Dynamic Host ConfigurationProtocol (DHCP) and assumes the role of the default gateway for all devices, regardless of location. That’s much more efficient than retrofitting entire inventories of devices across their global network and more cost-effective.
- Don’t allow microsegmentation to get stalled as a project; go after zero trust wins at the network level. Mapping application workflows and defining the many integration points across the hundreds of enterprise apps a typical organization relies on is where microsegmentation pilots lose momentum. Gartner VP Analyst Andrew Lerner writes that “network segmentation projects last longer than CISOs” in his blog post on network segmentation. Airgap is designed to scale at speed across enterprises by following the model of telco subscriber networks where breaches are rare and global scale is designed in at the network level at a very low cost. Air gapping every endpoint brings enterprises zero trust across their inventory of IT, OT, and IoT devices, drastically reducing their attack surfaces.
Conclusion
Don’t be satisfied having cybersecurity in passable shape; resolve to get it in zero trust shape. Simply put, that means implementing least-privileged access, protecting identities as the new security parameter, and, most importantly, reducing attack surfaces using microsegmentation.
The cornerstone of zero trust is based on assuming all entities are untrusted by default, least privilege access is enforced on every resource and identity, and comprehensive security monitoring is implemented. The bottom line is that microsegmentation, like zero trust, doesn’t need to be expensive or complex to be effective.
